Overwrite and BadChars
I wrote a script for Bad chars and show how I overwrite the program. This is all leading up to finding the right module and then gaining shellcode. Exploit Development is defiantly something I want to take some more time to get to know. I plan on going through these videos at least one more time.
So a couple things to remember is take out "\x00" and make sure you wrap it in "()"
Here is the first code I wrote
And here is the correct code. Anyone catch the mistake? Thats right line 9 I forgot to change.
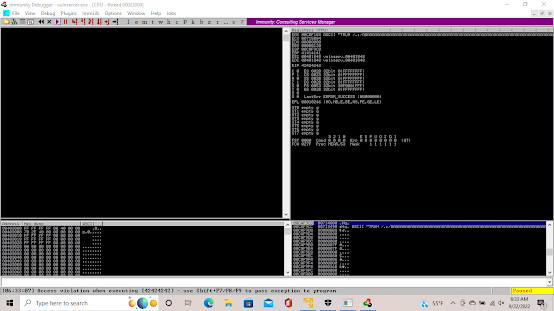
Now remember like with all the lessons before we are running both vulnserver and immunity debugger as admin. Attaching vulnserver to Immunity Debugger and pressing play. The goal is to overflow the buffer space and through the EBP (Extended Base Pointer) and into the EIP (Extended Base Pointer Instructional Pointer). Which is where we will be placing the malicious code.
And as you can see it is now paused meaning we gained overflow and crashed the machine.
The next lesson we will make sure we are in the right module and then gain actual shellcode.






Comments
Post a Comment