Spiking and Fuzzing
Here we started getting an introduction to some new tools. Using vulnserver, and immunity debugger. We did this as an introduction to exploit development. So the first thing you need to do is go out and download both vulnserver and immunity debugger.
Now that you've done that run both vulnserver and immunity debugger as administrator
Then attach vulnserver to immunity debugger and press play. Make sure in the bottom right it says "Running"
Here we use "nc" and "-nv" with the ip address of the target server with a port of 9999 to gain access and then we used 'HELP" to print out all the valid commands.
Here we use the command "generic_send_tcp" with our ip address and por 9999 and trun.spk. Now to be honest I dont 100% remember what the following2 zeros are for as this was a few weeks ago and like many people I dont remember every single detail (hence the screenshots and this blog)
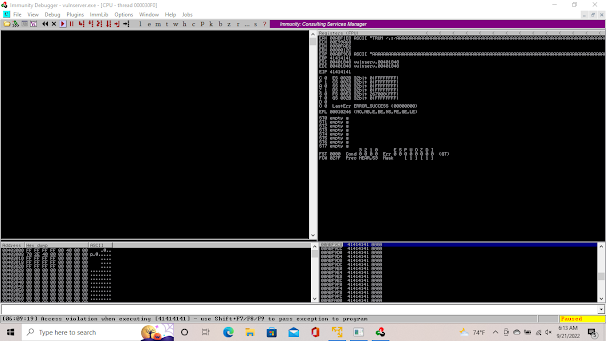
And here you see its paused again because we have just crashed the machine.
Now down below we are going to show our process in fuzzing. It is a fairly similar process to what we just did which is why I decided to combine them. The first 2 steps are exactly the same. Run vulnserver and immunitydebugger as admin and connect the two together.
On this one we must write a python script. So a few things to note we import "sys, socket" and we define the time. Then we create a buffer and a while true statement.
Now dont forget to "chmod".
Run your python script and notice it tells you where it crashed at, mine was 2900 bytes. This is an important piece of information as we are going to use it in the next couple lessons.
And as you can see in immunity debugger, it is paused due to crashing the server










Comments
Post a Comment