The Dev Exploit
This is the Dev machine through TCM's Practical Ethical Hacking course.
Here we did the same thing as the last box "dhclient" and "ip a"
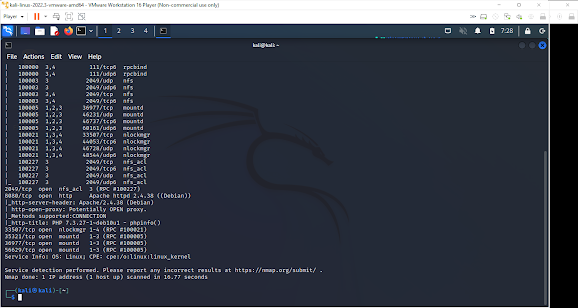
Here we run "nmap" to find open ports. This is the fourth or fifth exploit and what I have realized is the first several steps, rather it's on a windows or Linux machine, is the same.
Here I showed all the ports because some of the important ports were a little out of site on the previous slide
Here we are obtaining some vital information.
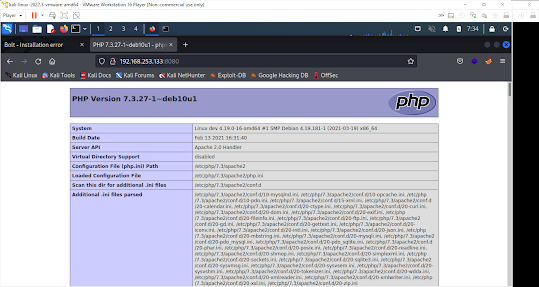
We were able to see the php page and get some good information.

Using "ffuf" again to gain some enumeration.
Here we used "searchsploit" for the first time. Now following this we used the information gathered to gain privilege escalation and captured the flag.







Comments
Post a Comment