Right Module then shell

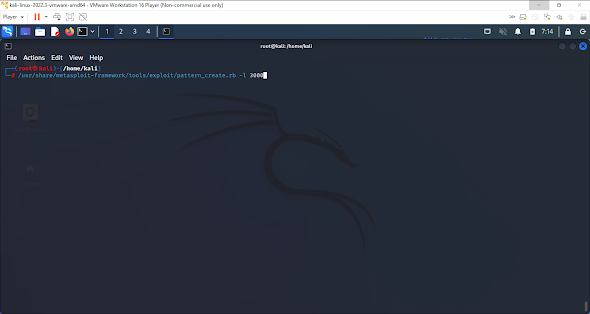
Finally we have made it. Here I will check we have the right module and then I will get my shell. Again remember these are just notes and not all of them. But if you see something and you know of a more effective way I am always up for hearing and learning new things So, line 4 we eventually get rid of but one thing to note is that on line 6 when type it into the script we are typing it backwards and only 2 characters at a time. Now I am sure there is a reason, and it is significant, but the course did not go into it. Here I am copying the payload after it was created. Now we add the payload to the script. This is the remainder of the script. Run this and we have completed the objective. Feel free to reach out on LinkedIn or Twitter